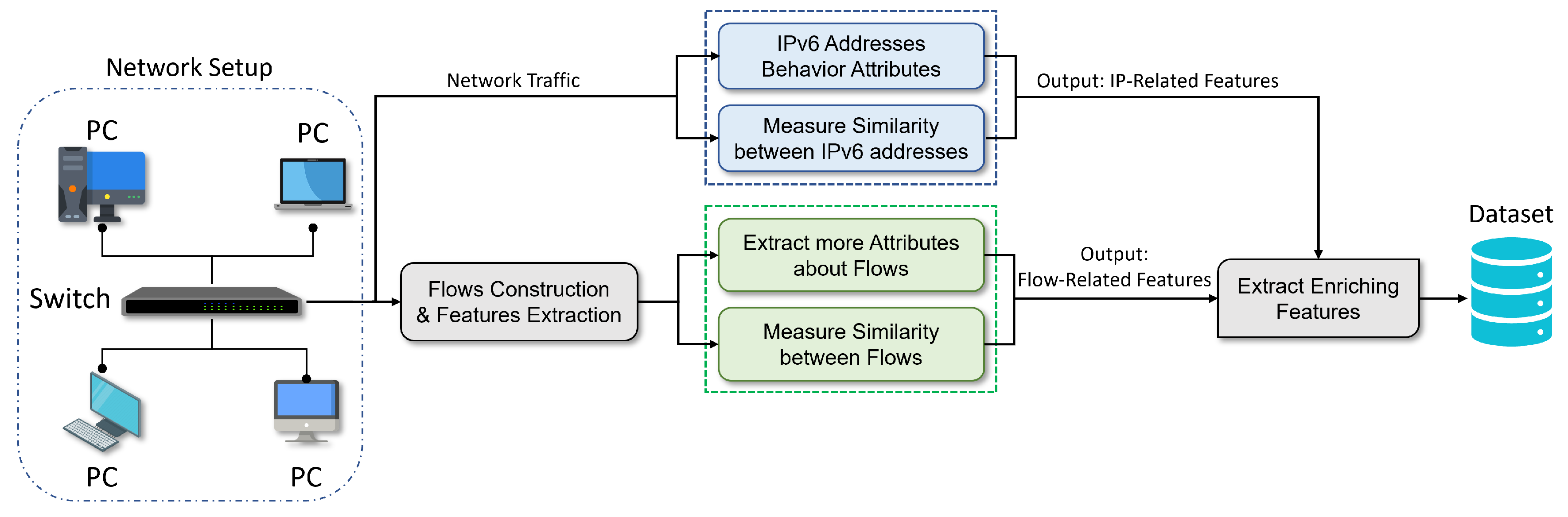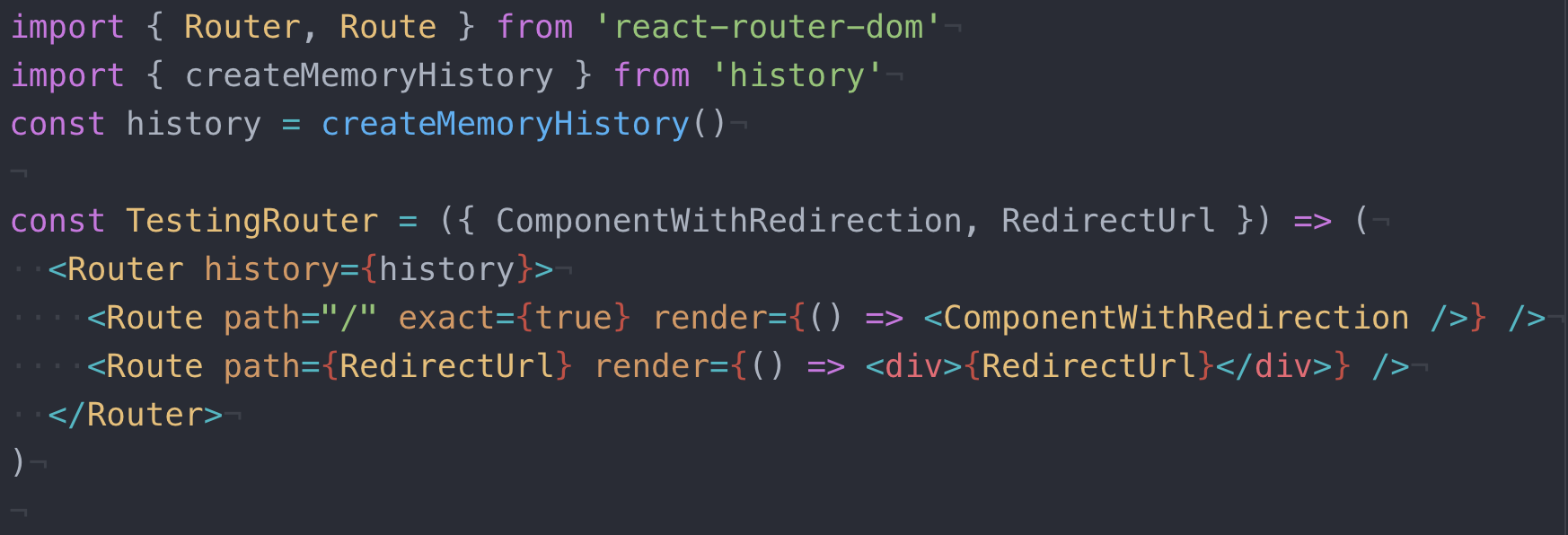
How to test <Redirect> from `react-router` with RTL (React Test Library) and JEST | by Ilya Zykin | Medium

Noroff School of technology and digital media added a cover video. | By Noroff School of technology and digital media | Facebook

USB Power Strip Surge Protector White Flat Plug 10ft Extension Cord 900j 10a240v for sale online | eBay

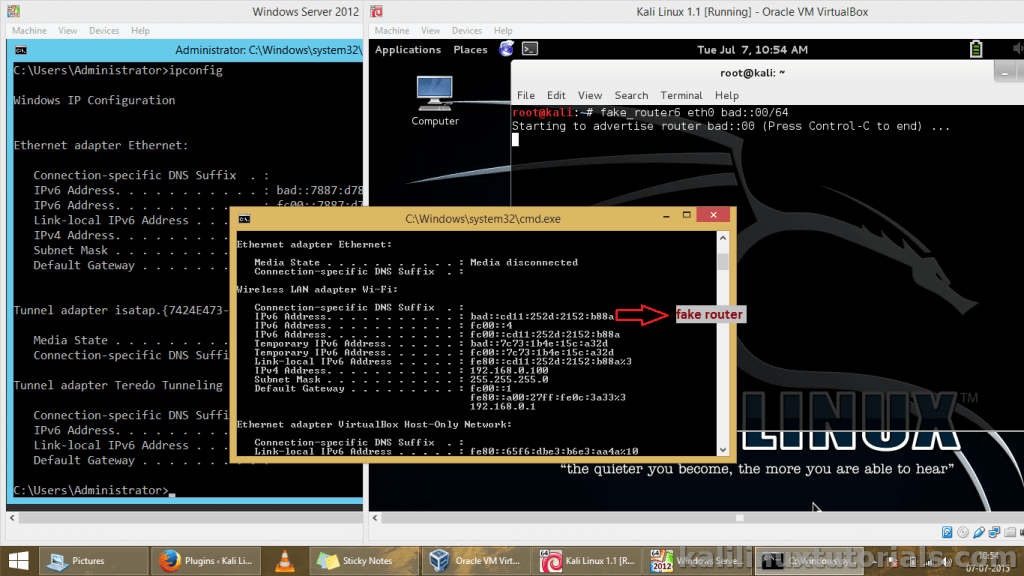
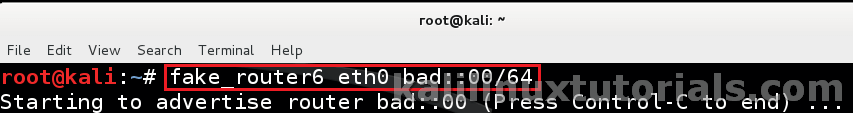
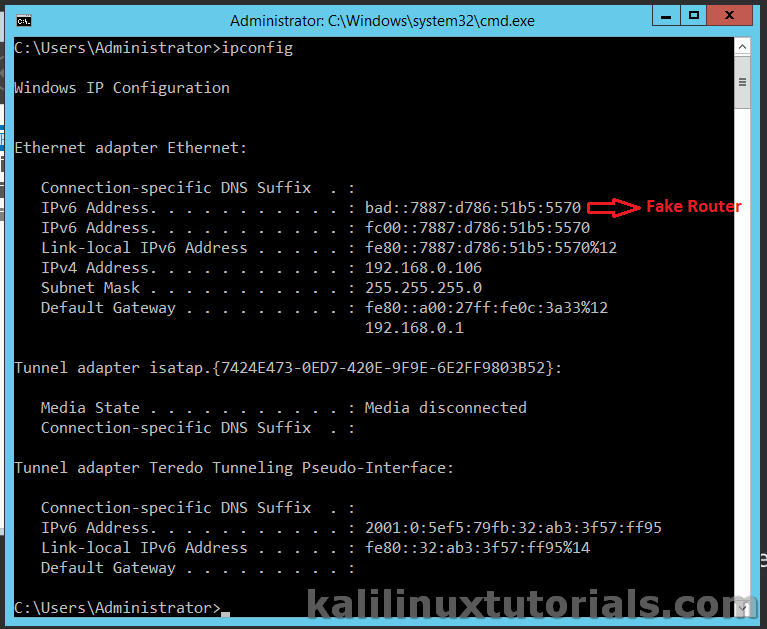
An Improved Secure Router Discovery Mechanism to Prevent Fake RA Attack in Link Local IPv6 Network | SpringerLink
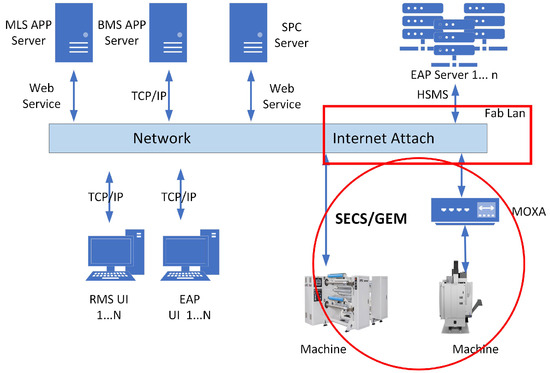
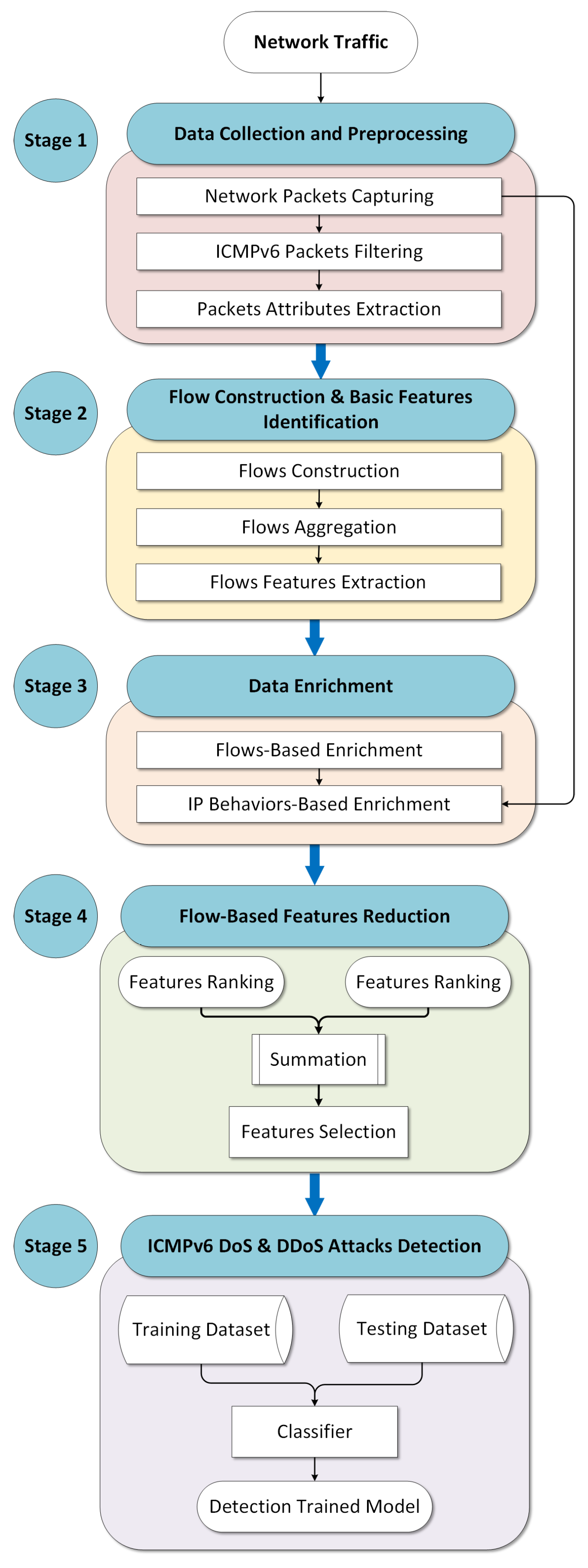
Sustainability | Free Full-Text | Replay-Attack Detection and Prevention Mechanism in Industry 4.0 Landscape for Secure SECS/GEM Communications

Online Safety and Awareness. Introductions We are students at UNM We are taking an Information Security course this semester. It is our mission to teach. - ppt download

An Improved Secure Router Discovery Mechanism to Prevent Fake RA Attack in Link Local IPv6 Network | SpringerLink
Suggestion] Packet Sniffing Card for Evil and Advanced Networking · Issue #1597 · MightyPirates/OpenComputers · GitHub